My DEF CON 33 experience
Published September 11th, 2025
👋 Introduction
I attended DEF CON 33 this year in Las Vegas and want to share a recap of my experiences and insights from the event. Whether you’re a seasoned security practitioner or just DEF CON-curious, I hope this gives you a helpful window into what goes on at one of the world’s largest hacker conferences.
Spoiler alert: AI dominated the conference discussions.
🎯 Why I attended
I went into DEF CON this year with a few goals in mind:
1️⃣ Stay up-to-date on emerging threats.
2️⃣ Find practical inspiration for our security workflows at LaunchDarkly.
3️⃣ Catch up with old friends and colleagues.
🔍 Favorite talks & villages
Talks
📍 Amplifying Phishing Attacks with Generative AI
-
Speaker: Daniel Marques
-
What it was about: This talk examined how AI allows threat actors to automate key phases of phishing campaigns, including initial reconnaissance, crafting targeted communications, and establishing attack infrastructure.
-
Why it stood out: Threat actors can now easily scale and customize phishing campaigns using AI, which was previously more challenging with manual methods.
📍 Zero Trust, Total Bust - Breaking into thousands of cloud-based VPNs with one bug
-
Speaker: David Cash & Rich Warren
-
What it was about: This talk highlighted how Zero Trust Network Access (ZTNA) solutions were exploited to bypass authentication, spoof device posture checks, and escalate privileges.
-
Why it stood out: This presentation aimed to highlight the vendor flaws of Zero Trust solutions. The key takeaway is to avoid blindly trusting your Zero Trust solution; consistently monitor logs and keep your infrastructure updated.
Villages
🧪 Red Team Village
-
What I explored: Modern red team tools and methodologies for penetration testers and red team engagements.
-
Key insight: I discovered some tools that I can leverage during our upcoming internal red team exercise for FedRAMP.
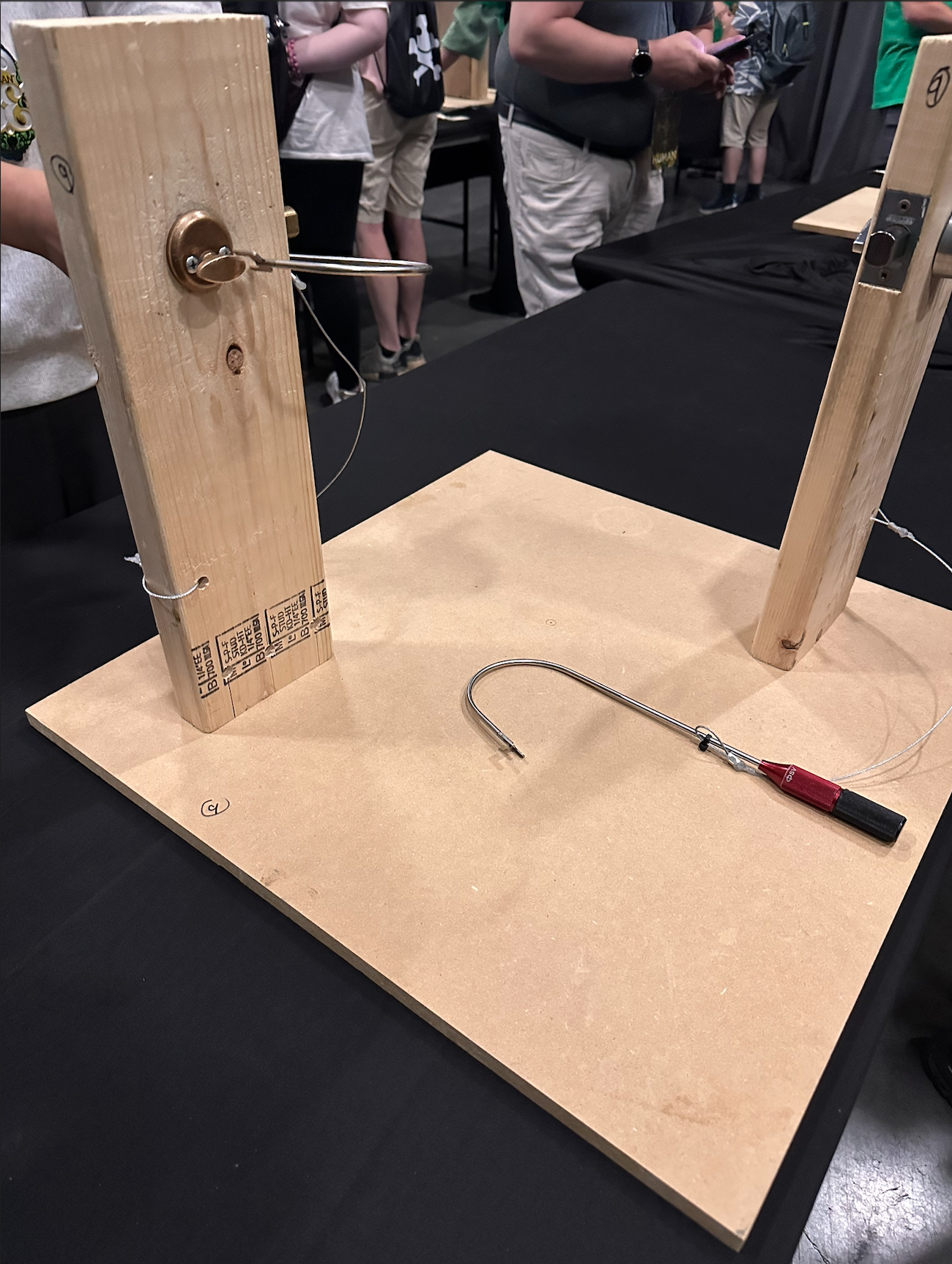
🧪 Physical Security Village
-
What I explored: This year I volunteered for the Physical Security Village despite having limited experience with physical penetration testing.
-
Key insight: I learned various lock bypass techniques and demonstrated them to other conference attendees.
🔒 Practical takeaways
Here are a few ideas or trends to dig into:
-
We should consider leveraging AI more to perform log analysis.
-
Prompt injections will become more prevalent with LLM adoption.
-
AI is enabling threat actors to launch hyper personalized, convincing, and adaptive phishing campaigns.
👀 Noteworthy quotes
Sources for these quotes were smart folks at a happy hour I attended, but I didn’t catch their names.
📸 Photo dump







My favorite badge this year was the Laser Tag Badge. Unfortunately, my IR emitter fell off on the first day of the Con. I soldered on a new one but finished 160th on the leaderboard.
💭 Final thoughts
This was my fourth DEF CON and it’s always a bit overwhelming—in the best way. It’s a reminder of the creativity, curiosity, and persistence that defines the security community. Whether you’re trying to break things or protect them, it’s all about asking better questions.
